What is AWS IoT?
AWS is a comprehensive and widely used cloud computing platform provided by Amazon. It offers a wide range of cloud services and tools that enable you to build and deploy applications and services with high scalability, flexibility, and reliability.
One of the services offered by AWS is AWS IoT (Internet of Things). AWS IoT is a collection of managed services that facilitate the integration and management of Internet of Things devices and data in a scalable and secure manner. It provides a set of services that help connect devices, collect and analyze data, and build IoT applications.
Some core components and features of AWS IoT include:
- Gateway: This component enables devices to communicate securely and efficiently with AWS IoT. It supports various protocols such as MQTT (Message Queuing Telemetry Transport), HTTP, and WebSockets.
- Regel engine: The rules engine enables processing of messages sent by devices and performs actions based on predefined rules.
- Analyse und Integration: AWS IoT integrates with other AWS services such as AWS Lambda, AWS IoT Analytics, and Amazon Kinesis so you can perform complex analytics, store and process large amounts of data, and trigger actions based on the analyzed data.
- Sicherheit: AWS IoT provides several security features to ensure the confidentiality, integrity, and availability of IoT data. It supports mutual authentication between devices and AWS IoT and encryption of data in transit.
Configuring the MQTT broker in the AWS portal
Each AWS IoT instance contains an MQTT broker to which Modbus Cloud Connect can connect. Authentication when establishing a connection is performed exclusively via certificates and not with a username and password (more on this later). Therefore, a certificate must first be created in the AWS portal and linked to a suitable policy. The certificate is created by clicking on “Add Certificate” in the “Security” section under “Certificates”. AWS generates several files, including a certificate, a public key and a private key. The certificate and private key need to be downloaded.Before we can upload them in the Self Service Portal of Modbus Cloud Connect, the extension ".key" needs to be removed from the two files so that they become ".pem" files.
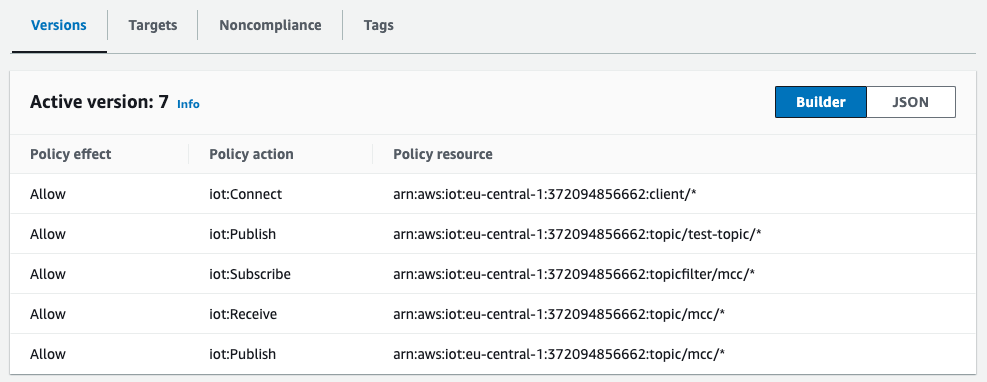
The policy is created under the Security section under the Policy.
The screenshot you can see an example configuration for a policy.
In the first line the permission is set to connect to the broker.
In the second line the permission to publish messages to all topics is set with the prefix “test-topic/”. With this a working policy has already been configured. The last three lines ensure that you can also use the MQTT back channel if needed (see Hands-on Modbus Cloud Connect – Instant Read & Instant Write via Narrowband-IoT).
For this, a subscribe right to all topics with the prefix “mcc/” was set, as well as the right to receive and publish these messages.
 Now this policy has to be linked with the just created certificate, which can be done in the settings of the certificate.
Now this policy has to be linked with the just created certificate, which can be done in the settings of the certificate.
Setup of the Modbus Cloud Adapter
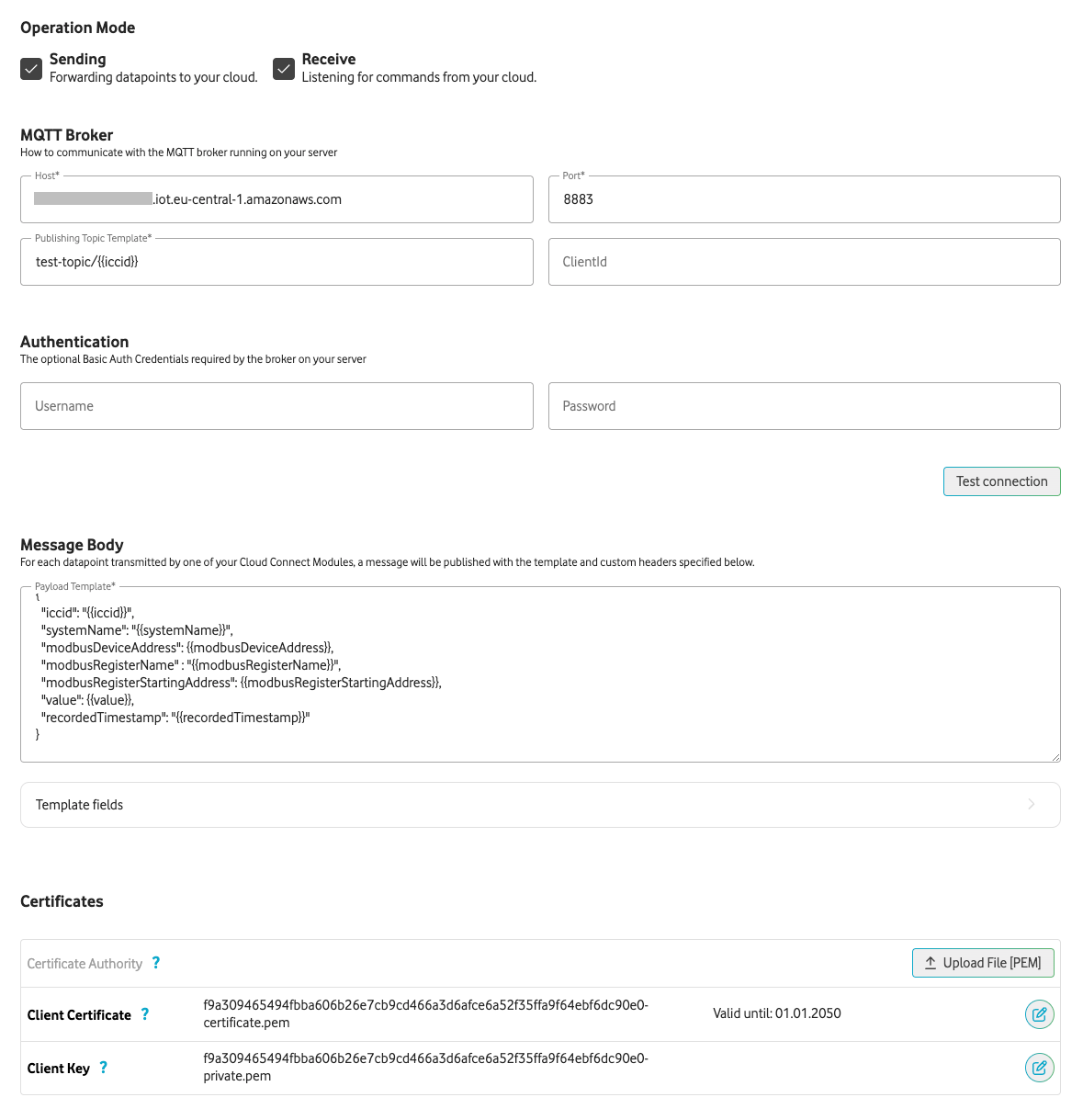
In order to establish the connection to this MQTT broker in the Modbus Cloud Connect self-service portal, a new MQTT Cloud Adapter must be created.The host of the broker is in the settings of AWS IoT under “Endpoint” and 8883 is used as port. The “Publishing Topic Template” must be selected so that it was allowed in the policy (example: test-topic/{{iccid}}). The client ID as well as username and password are left empty. Under “Certificates” the certificate and the private key must be uploaded. It is not necessary to specify a Certificate Authority because AWS uses one of the generally accepted root CAs.
What do you use certificates for?
Passwords are vulnerable to various types of attacks, such as phishing, brute force, or reusing passwords on different platforms. An alternative is to use certificates in conjunction with TLS (Transport Layer Security) with Client Authentication.
Client Authentication with TLS not only ensures the identity of the server, but also that of the client. This provides additional security and authentication on both sides of the communication. To achieve this, the client needs a certificate and a public and private key.
The client’s certificate must be signed by a trusted certificate authority that the server trusts. These certificate authorities confirm the identity of the client and ensure that the certificate is valid. In turn, the server can be sure that the client authenticating with a particular certificate is legitimate.
The use of certificates offers several benefits:
- Stronger authentication: The use of certificates is based on asymmetric encryption technology, which provides a higher level of security than traditional passwords. The private key associated with the client’s certificate is secret and cannot be easily guessed. This reduces the risk of attacks such as brute force.
- Protection against phishing: The use of certificates reduces the risk of phishing attacks. With Client Authentication using TLS, the server is able to verify the client’s certificate and ensure that it has been signed by a trusted certificate authority. This prevents an attacker from using a forged certificate to impersonate a legitimate client. For a successful attack, an attacker would need to gain access to the private key of the valid certificate. Since this is (usually) never transmitted over the Internet, a successful phishing attack is unlikely.
- Unique identity: Each client has a unique certificate that has been signed by the certificate authority. This ensures that each client has a unique identity and does not reuse the same credentials on different platforms.
The MQTT broker integrated in AWS IoT uses this type of authentication and offers the option of having the certificates generated automatically in the AWS portal.
Modbus Cloud Connect is easy to deploy, flexible in connectivity, and versatile. Your device, directly to the cloud.


 Now this policy has to be linked with the just created certificate, which can be done in the settings of the certificate.
Now this policy has to be linked with the just created certificate, which can be done in the settings of the certificate.